Unfortunately, the threat of cyber attacks looms large over individuals, businesses, and organizations of all sizes. It seems like there is a new report in the news everyday of a business being targeted and your personal data being exposed to hackers. Businesses big and small are being affected more than ever as the hackers have increased their sophistication and frequency of cyber crime. What was once targeted at larger companies with large amounts of data, the prevalence of artificial intelligence has made it easier for these crooks to hit more businesses with more frequency which has allowed them to attack smaller businesses. If you own a business of any size in Texas, and aren't nervous yet. Well pardner. You should be.
A cyber attack refers to any malicious attempt to exploit vulnerabilities in computer systems, networks, or devices to gain unauthorized access, disrupt operations, steal sensitive data, or cause other harmful consequences. These attacks can take various forms, such as phishing scams, social engineering tactics, malware infections, denial-of-service (DoS) attacks, and beyond. Unfortunately, cyber incidents can target anyone - from multinational corporations to small doctors' offices. This serves as a stark reminder that no one is immune, and even the smallest entities are at risk if they are not vigilant in protecting themselves against cyber threats.

What are the risks of data loss from a cyber attack?
While not the only cyber risk, one of the largest cyber risks today is the risks of data loss. Cyber threats have become increasingly sophisticated, posing significant challenges to the security of our valuable and sensitive data. These attacks not only target individuals but also organizations, from small businesses to large corporations, and even the government.
One particular cyber crime is the theft of sensitive data. Malicious actors gain unauthorized access to systems and networks, extracting valuable information such as personal identities, financial records, medical records, and intellectual property. This data breach can have devastating consequences for individuals and businesses alike, leading to financial loss, identity theft, or reputational damage.
Another danger lies in the disruption of systems and networks. Cyber attacks, such as ransomware or distributed denial of service (DDoS), can render an organization's operations paralyzed, causing significant downtime and financial impact. This can be particularly detrimental in critical sectors like healthcare, where patient care and safety are at stake, and the loss of access to data can mean the difference between life and death.
Also, cyber attacks have the potential to compromise national security. Attacks on government agencies and critical infrastructure systems can disrupt essential services, compromise classified information, and undermine trust in institutions. We've recently seen this in Dallas with the shutdown in the 911 system after an attack.
Given these risks, it is crucial for organizations and individuals to prioritize data security. Investing in robust cybersecurity measures, such as firewalls, multi-factor authentication, encryption technologies, and employee awareness training, can help mitigate the impact of these cyber risks. Additionally, proactive incident response plans and regular data backups are essential for ensuring business continuity and making sure that a disruption of operations doesn't cripple your business.
The risks of data loss from cyber attacks are significant. The increase in cyber threats threatens valuable and sensitive data, disrupts systems and networks, and compromises national security. To safeguard against these risks, organizations and individuals must prioritize data security and adopt comprehensive cybersecurity measures. Let's look at some specific types of cybersecurity attacks.
Types of Cyber Attacks
From small businesses to large enterprises, no one is immune to the threat of malicious actors seeking to exploit vulnerabilities in systems and networks. This can stem from a seemingly harmless phishing scam resulting in the compromise of electronic medical records (EMR) data. Or it could be as complex as malware sitting on your exchange server waiting to manipulate an invoice. The types of cyber attacks are vast and varied, and it is imperative for individuals and organizations to understand the different tactics employed by cyber criminals in order to better protect themselves.
Malware Attack
A malware attack is a type of cyber threat that involves the use of malicious software to harm a computer system or network. Malware, short for malicious software, is specifically designed to cause damage, steal information, or disrupt the normal functioning of a system.
Malware can take various forms, such as viruses, worms, Trojan horses, ransomware, spyware, and adware. Each type has its own specific method of infecting a system and carrying out its malicious activities.
One of the primary goals of a malware attack is to block access to a system or network. This can be achieved through techniques like encrypting files or denying access to important resources, effectively locking out the legitimate users.
Another objective of malware is to obtain information from the compromised system. This can include sensitive and personal data, such as financial information, login credentials, or personal identifying information. This stolen data can then be used by cyber criminals for various fraudulent activities.
Also, malware attacks can disrupt the functionality of a system, causing it to crash, freeze, or become slow. It can also be used to install other harmful software, creating a gateway for additional cyber threats.
It is important for individuals and organizations to stay vigilant and take proactive measures to protect against malware attacks. This includes keeping software and systems up to date, using strong and unique passwords, regularly backing up data, implementing security measures such as firewalls and antivirus software, and educating users about the risks and best practices to mitigate the threat of malware attacks.
Phishing Attack
Cyber threats are constantly evolving with new techniques and tactics used by cyber criminals to target individuals and organizations. One of the most prevalent forms of attack is phishing, a type of email-borne attack that aims to trick unsuspecting victims into revealing confidential information or downloading malware.
Phishing attacks rely on social engineering tactics, using psychological manipulation to deceive users into clicking on malicious links or providing sensitive information. These emails often appear to be legitimate, mimicking the branding and language of reputable organizations. They may even claim urgent action is required or offer enticing incentives to entice victims to take the bait. Haven't we all received an email from "Amazon" that looks mostly legit, but comes from a weird email address upon inspection?
Once a victim falls for the deception and clicks on a malicious link or downloads an infected attachment to connected devices, their system becomes compromised. This can lead to a range of detrimental consequences, including the theft of login credentials, financial information, or other personal data. Cyber criminals can use this information for various illicit activities, such as identity theft, financial fraud, or even selling the data on the dark web to other malicious actors.
The frequency of phishing attacks has been increasing steadily, with cyber criminals employing ever more sophisticated techniques to bypass security measures. It is vital for individuals and organizations to remain vigilant and exercise caution when interacting with emails, especially those containing suspicious attachments or requesting personal information. Implementing robust cybersecurity measures and educating users about the dangers of phishing attacks is essential in mitigating the risks and protecting sensitive data.
Phishing attacks pose significant cyber risks to individuals and organizations alike. With cyber criminals constantly refining their techniques, it is paramount for everyone to stay informed and adopt defensive measures to safeguard against these email-borne attacks. By remaining cautious and understanding the characteristics and impact of phishing attacks, we can minimize the potential damage and protect ourselves from falling victim to these malicious schemes.
Denial of Service (DoS) Attack
In the world of cyber threats, one of the most disruptive and damaging attacks is the Denial of Service (DoS) attack. This type of attack aims to render a system or network unavailable to its intended users by overwhelming it with an overload of demand.
In a Denial of Service attack, the attacker takes control of multiple devices to flood the targeted system with an overwhelming amount of traffic. This flood of traffic exceeds the system's capacity to handle the requests, resulting in a complete or partial denial of service to legitimate users trying to access the system.
To make matters worse, attackers have become increasingly sophisticated in coordinating these attacks. Distributed Denial of Service (DDoS) attacks involve multiple compromised devices, forming a botnet, which can be controlled remotely by the attacker. This allows for a more extensive and widespread assault on the target.
The impact of a successful DoS or DDoS attack can be severe, especially for organizations that rely heavily on their online presence. It can result in financial losses, reputational damage, and even compromise critical services, such as e-commerce transactions or healthcare systems.
Preventing DoS attacks requires understanding and addressing vulnerabilities in a system's architecture, such as implementing proper firewalls, load balancing mechanisms, and traffic filtering. Additionally, utilizing network monitoring tools and staying informed about current attack techniques can help organizations better protect themselves against these malicious acts.
Social Engineering Attack
Social engineering attacks are a prevalent and concerning form of cyber attack that hackers use to exploit human psychology and trick individuals into disclosing sensitive information. These attacks often take the form of phishing attacks, where hackers create emails that appear genuine and trustworthy, resembling communications from legitimate sources.
To protect against social engineering attacks, it is crucial to train employees to recognize and avoid falling for these deceptive tactics. By educating staff on how to identify suspicious emails, websites, or phone calls, organizations can significantly reduce the risk of falling prey to these attacks. This training should emphasize the importance of never sharing sensitive information, such as login credentials or financial details, without understanding and verifying the legitimacy of the request.
Social engineering attacks exploit human psychology to deceive individuals and gain access to sensitive information. It is imperative for organizations to invest in training their employees to recognize and thwart these deceptive tactics, as the consequences of falling victim to such attacks can be severe.
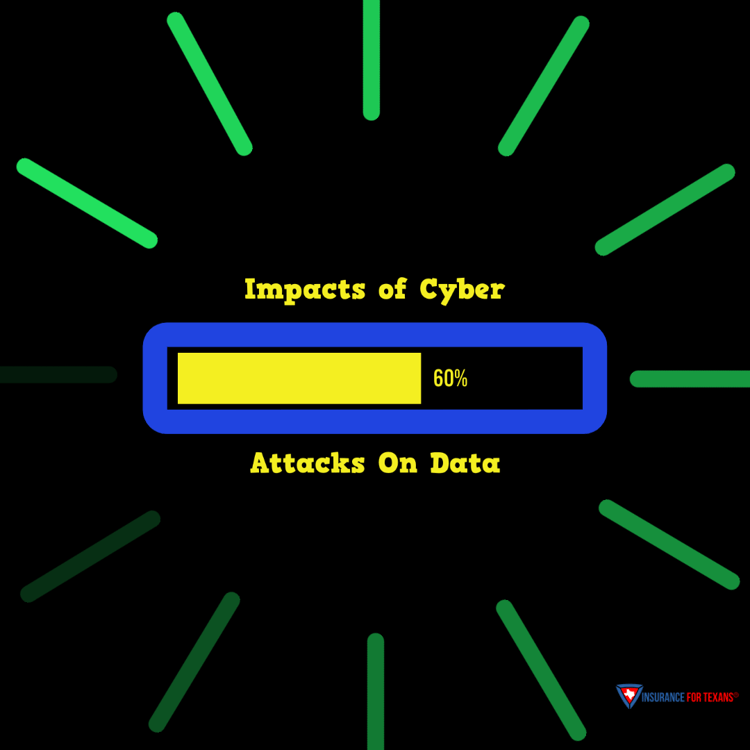
Impact of Cyberattacks on Data Protection and Privacy
The impact of cyberattacks on data protection and privacy cannot be underestimated. The consequences of cyber attacks can be devastating, resulting in compromised personal information, financial loss, and damage to an organization's reputation. As technology continues to advance, so do the tactics employed by cybercriminals, making it imperative for businesses and individuals to prioritize data security and take proactive measures to mitigate the risks of cybersecurity issues.
Loss of Confidential Information
The loss of confidential information through data breaches can result in severe risks and consequences. One example is the LinkedIn data breach in 2012, where approximately 6.5 million user passwords were compromised. This breach not only exposed users to potential identity theft but also damaged LinkedIn's reputation and resulted in financial losses for the company.
Another notable incident is the recent attack on Microsoft's Exchange Server software, where malicious actors exploited vulnerabilities to gain unauthorized access. This breach not only highlighted the significance of timely software updates but also highlighted the risks of putting critical infrastructure at stake.
The Colonial Pipeline ransomware incident further underscores the consequences of data breaches. It resulted in a halt to the fuel supply chain, causing panic buying and escalating fuel prices. This incident exemplifies the significant economic impact and disruption that organizations and even entire industries can face due to data breaches.
The risks associated with the loss of confidential information are not limited to large corporations. We have seen cases of a Texas doctors' offices being hacked via a phishing scam that serves as a reminder that even small offices can fall victim to cyber risks if they are not vigilant.
Data breaches can lead to various consequences, including financial losses, reputational damage, regulatory fines, and customers losing trust in the affected organization. To mitigate these risks, it is crucial for businesses to invest in robust cybersecurity measures, such as regular software updates, employee education, and incident response plans.
The examples of well-known data breaches highlight the magnitude of the problem and underscore the urgent need for proactive cybersecurity measures to safeguard sensitive data from human error, potential insider threats, and cybersecurity breaches.
Risk to Brand Reputation
If your local healthcare organization was to fall victim to a devastating common cyberattack, you would be irate. However, the consequences of such attacks extend far beyond the breach itself. One crucial aspect that is often overlooked is the significant impact on brand reputation.
When a company suffers a cyber attack, the trust of its customers is shaken. News spreads quickly, and consumers become wary of doing business with an organization that has a history of compromised data. This loss of trust can be devastating and often leads to a shift towards competitors who are perceived as more secure. This means that the average cost of a data breach can extend well beyond the regulatory cost of cybercrime or even the financial gain of these cyber criminals.
Consumers are becoming increasingly aware of the potential risks associated with their personal information falling into the wrong hands. In the face of these cyber vulnerabilities, customers may question your company's ability to protect their data and may even doubt the overall security of the industry. Especially if you are a healthcare organization or financial institution.
To safeguard both customer data and brand reputation, it is crucial for businesses of all sizes to prioritize robust cybersecurity measures. This includes regular software updates, employee education on best practices, and the implementation of incident response plans. By actively investing in cybersecurity ventures, companies can demonstrate their commitment to protecting customer data and help alleviate consumer concerns about the risk of data breaches.
Financial Losses Due to Data Breaches
Data breaches can have severe financial consequences for businesses. These breaches not only require the investigation and remediation of the incident but also the costly process of notifying affected customers and implementing stronger security measures. These financial burdens can quickly add up for businesses, especially smaller ones with limited resources. The average data breach cost grows with each layer of compliance that your company requires.
The costs incurred as a result of data breaches extend beyond the immediate aftermath. Companies often face legal and regulatory fines, as well as potential lawsuits from affected individuals. The damaging impact on brand reputation can also result in a loss of revenue and market share. The correlation between data breaches and consumer perception of cybersecurity risk is undeniable. Consumers are increasingly aware of the potential risks associated with their personal information falling into the wrong hands, and they prioritize doing business with companies that can protect their data.
It is crucial for organizations, regardless of their size, to implement strong cybersecurity measures to protect sensitive data and safeguard their financial well-being.
Legal Implications of Data Loss
Data loss resulting from cyber attacks carries significant legal implications for organizations. When sensitive data, such as personal or financial information, is compromised, businesses may face serious consequences.
Firstly, organizations can be held liable for failing to protect customer data, violating legal obligations and industry regulations. For instance, the Equifax breach in 2017 resulted in a $700 million settlement with the Federal Trade Commission due to the company's failure to implement adequate security measures. Such regulatory fines can have a substantial financial impact on organizations.
Additionally, data breach victims may seek legal recourse by filing lawsuits against the affected organization. These lawsuits can result in substantial monetary compensations that businesses must pay to affected individuals. The cost of defending against these lawsuits, combined with potential settlements, can be overwhelming.
In addition to these items, your business can be required to provide credit monitoring services to the affected parties for a period of time which will also raise your average cost of a breach. When we think about cyber security threats, this sort of legal activity may not enter into a business owner's through process.
To mitigate the legal implications of data loss, organizations must prioritize implementing robust protections against cyber risks, regularly monitoring for threats, and promptly responding to incidents. Proactive measures can help minimize the risk of data breaches and protect organizations from potential liabilities and legal consequences. And as you are well aware, an ounce of prevention is worth a pound of cure. And that has never been more true than it is with cybersecurity ventures!

How to Mitigate Attacks and Not Be A Cybersecurity Statistic
Whether you're in a small doctors' office in Texas or Fortune 100 Company, a seemingly harmless email can lead to a devastating cyber attack. Clicking on a phishing link can open the door for hackers to gain access to sensitive data, private networks, debit card information, or destructive attacks on your organization. And the consequences can be severe.
To mitigate cyber attacks and protect data, organizations must prioritize best practices and strategies. One crucial step is educating staff about different types of cyber risks. By training employees to identify and avoid suspicious emails, links, or attack vectors, organizations can strengthen their first line of defense.
Multifactor authentication is another essential measure. By requiring multiple forms of verification, such as a password and a unique code sent to a mobile device, organizations can add an extra layer of protection to their systems and data. Especially since employees can let their guard down on personal devices which are regularly used for business email compromises.
Regular penetration testing is vital to identify vulnerabilities within a network or infrastructure. By simulating real-world cyberattacks, organizations can discover weak points and address them promptly, reducing the risk of successful breaches or denial of service attacks.
Monitoring threat intelligence is essential for staying ahead of evolving cybersecurity threats. By staying informed about the latest tactics used by bad actors, organizations can proactively implement defensive measures to safeguard their data.
It's crucial for businesses to understand prevalent cyber risks, including phishing attacks, malware attacks, and denial of service attacks. With this knowledge, your business can develop comprehensive cybersecurity protocols tailored to their specific needs.
How Can I Get Help?
There are multiple ways to mitigate your Cyber Risks, and one of those is to have an audit done on your system. If your business has never considered your cyber security risks, Insurance For Texans is happy to help you with a free cyber critical vulnerability report that is provided by our insurance partners in the cybersecurity industry. That is a great first step to understanding your risk and taking steps to reduce it. We also work with cyber security professionals who can help business owners put plans in place to secure your network and reduce the risk of business email compromises.
To get started, simply click the button below. Our independent agents are here to help you whether you're a manufacturer or in the healthcare industry. We have the experience and expertise to help you formulate not an insurance plan, but also a risk mitigation plan to function as a business partner to you.



