When we hear of cyber crimes there are a lot of eyeballs that glass over. We think it couldn't happen to us. That happens to someone huge like the MGM Grand cyber attack in Las Vegas recently. It causes us to let our guards down if we're being honest with ourselves. BUt it only takes one tiny mistake to create a massive loss to our own business. Let me show you how.
I was sitting at my desk working on preparing insurance for one of our clients when a notification from PayPal went off on my phone. Because I have several subscription payments set up through them, it didn't seem uncommon. But when I began to look at the notification, it was for an invoice that I did not recognize. The invoice, sent through the PayPal app, obviously looked legit, but was from a source that I did not recognize. They were simply attempting to get me to hit the pay button.
But they then took it a step further. There was an email that was pushed through to me that showed that they had actually received funds. They wanted me to call a toll free number to resolve the dispute. Obviously, this was an attempt to get me to call the number so that they could attempt to get valuable account data from me. This was not that difficult to attempt on their end, but could be disastrous on mine!
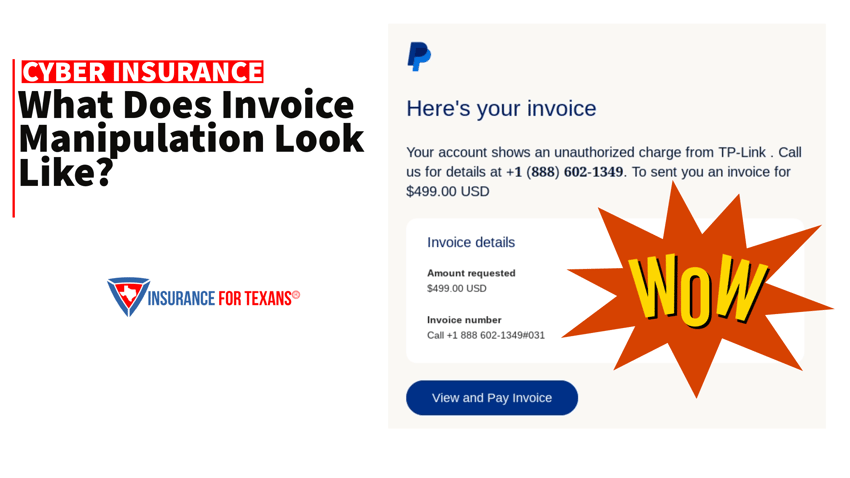
When we think of cyber attacks, and invoice manipulation especially, we may not be exactly sure what that looks like. So here is a quick rundown on what you can keep a watchful eye out for so that you do not fall prey to an attack like this.
Invoice Manipulation Definition
Invoice manipulation refers to the fraudulent alteration or manipulation of invoices in order to deceive individuals or organizations into making incorrect payment arrangements. This type of fraudulent activity can occur in various ways, including the manipulation of payment details, creation of fake invoices, or the submission of duplicate invoices for payment. Invoice manipulation is a common type of fraud that can have significant financial consequences for businesses. In some cases, bad actors may use social engineering techniques, such as business email compromise, to trick employees into making fraudulent payments or providing sensitive financial information. To protect against invoice manipulation, businesses can implement internal control measures and multi-factor authentication for their accounts payable processes. Additionally, comprehensive cyber insurance coverage can provide financial protection in the event of invoice frauds or other cyber threats.
Common Types of Fraud
Invoice Fraud is a prevalent form of financial crime that affects businesses of all sizes and industries. It can take various forms, but some common types include vendor impersonation, invoice manipulation, duplicate invoices, and approval risk. Let's take a look at each.
Vendor Impersonation
This occurs when a fraudster poses as a legitimate vendor and submits fake invoices for payment. They typically target businesses with lax accounts payable processes and payment controls and provide false payment details to divert funds to their own accounts.
Invoice Manipulation
Involves altering existing invoices to generate additional funds. Fraudsters may change payment amounts, add unauthorized charges, or modify bank account details to divert payments to their own accounts.
Duplicate Invoices
Occurs when multiple invoices are submitted for the same goods or services rendered. Fraudsters take advantage of busy accounts payable teams and systems that lack proper controls to submit fraudulent duplicate invoices and receive payments multiple times.
Approval Risk
This refers to the vulnerability of the approval process for invoices. Fraudsters exploit weak internal controls and lack of segregation of duties to manipulate invoice approvals, bypass safeguards, and authorize fraudulent payments.
To protect against these common types of invoice fraud, businesses need to implement strong internal controls, such as multi-factor authentication for payment details, regularly review and verify invoices and payment requests, and train employees to recognize fraudulent activity.
Who Are Bad Actors Involved in Invoice Manipulation
Bad actors involved in invoice manipulation are individuals or groups who engage in fraudulent activities to deceive businesses and manipulate invoice payments. These perpetrators employ various methods and have different motivations for carrying out these deceptive practices.
Hackers are one category of bad actors who target businesses' email accounts or financial systems. They gain unauthorized access to these platforms and manipulate invoices by altering payment amounts or changing bank account details. Their motivation is typically financial gain, as they divert funds to their own accounts.
Impersonators are another type of bad actor involved in invoice manipulation. They pose as legitimate vendors and submit fake invoices, providing false payment details to divert payments to their own accounts. Impersonators often target businesses with weak accounts payable processes and payment controls.
Phishing attackers are yet another category of bad actors in this realm. They employ social engineering tactics to obtain sensitive information, such as login credentials or financial data, from unsuspecting individuals. By impersonating legitimate vendors or business partners, they manipulate invoices and payment instructions to deceive businesses into making fraudulent payments.
These bad actors manipulate invoices and payment instructions to deceive businesses into making payments to their own accounts. Their methods include altering invoice details, using false payment details, submitting fake invoices, or tricking individuals into transferring funds to fraudulent accounts. What a bummer, right?
What Are The Effects of Invoice Manipulation
Invoice manipulation can have severe effects on businesses, leading to substantial financial losses and liabilities. This type of fraud can result in businesses making payments to fraudulent bank accounts, causing the diversion of funds intended for legitimate vendors or suppliers. The financial impact can be significant, particularly if large sums of money are involved or if the manipulation goes undetected for an extended period.
Recovering stolen funds or goods can be challenging for businesses affected by invoice manipulation. The funds are often transferred to offshore accounts, making it difficult to trace and retrieve them. Additionally, the goods or services associated with the manipulated invoices may have already been delivered or provided, making recovery even more complex.
Prosecuting perpetrators of invoice manipulation can also present challenges. In many cases, these bad actors operate from overseas jurisdictions, making it difficult to hold them accountable or bring them to justice. The costs involved in pursuing legal action and the complexities of international legal systems further hinder successful prosecution.
Given the potential financial risks and difficulties in recovering losses through traditional means, business owners must consider insurance coverage against invoice fraud. Comprehensive cyber insurance policies can provide coverage for financial losses resulting from invoice manipulation. This coverage can help mitigate the financial impact on businesses and provide assistance in the recovery and investigation processes.
Prevention and Detection of Invoice Manipulation
Since invoice manipulation can have devastating financial consequences for businesses, the best thing to do is avoid being trapped in it altogether. To mitigate the risk of falling victim to this form of fraud, organizations need to implement preventive measures and establish robust detection systems. Prevention begins with implementing strong internal controls, such as segregating duties and implementing multi-factor authentication for payment processes. It is important to thoroughly vet and validate new vendors or make changes to existing vendor information. Regularly reviewing and reconciling accounts payable and monitoring for any unusual or suspicious activity can also help detect potential instances of invoice manipulation. Additionally, leveraging technology solutions like automated invoice processing systems and invoice approval workflows can add an extra layer of protection against fraudulent invoices. By implementing preventive measures and establishing effective detection systems, businesses can strengthen their defenses against invoice manipulation and minimize the potential financial impact.
Strengthening Internal Controls
Strengthening internal controls is essential to prevent invoice manipulation and ensure the accuracy and integrity of invoice processing. Implementing stringent processes and procedures can help businesses safeguard against fraudulent activities and minimize financial losses.
One effective measure is to segregate duties within the accounts payable department. By assigning different individuals to handle various stages of the invoice processing workflow, such as invoice receipt, verification, and approval, the risk of unauthorized access and manipulation is significantly reduced. This segregation also creates a system of checks and balances, where multiple individuals are involved in the approval process, ensuring a higher level of accuracy and accountability.
Implementing authorization levels is another crucial aspect of strengthening internal controls. By establishing clear guidelines on who has the authority to approve and process invoices, businesses can prevent unauthorized access and manipulation. Different levels of authorization can be assigned based on the invoice amount or vendor category, allowing for greater control and reducing the chances of fraudulent activity.
Regular audits and reviews of invoice processing procedures are also important in maintaining internal controls. These audits can help identify any weaknesses or vulnerabilities in the system, allowing businesses to implement necessary improvements and updates. Ongoing monitoring of invoice activity, both manually and through automated systems, can further enhance control and detect any suspicious or abnormal activities.
By prioritizing internal controls through the implementation of stringent processes and procedures, businesses can effectively mitigate the risks associated with invoice manipulation. This not only protects against financial losses but also ensures the integrity and accuracy of financial transactions.
Monitoring Financial Transactions
Monitoring financial transactions is a crucial preventative measure to safeguard businesses against invoice manipulation. Regularly reviewing and reconciling invoices, payments, and bank statements plays a pivotal role in detecting any irregularities or suspicious activities.
By closely monitoring financial transactions, businesses can identify any discrepancies between the amounts billed on invoices and the actual payments made. This process helps to ensure that invoices are legitimate and accurate, minimizing the risk of fraudulent activity. Additionally, vigilant monitoring enables businesses to track the frequency of invoices from specific vendors, identifying any sudden increases or duplicate invoices that may indicate fraudulent behavior.
Reconciliation of invoices, payments, and bank statements is an effective way to cross-reference data and detect any inconsistencies or fraudulent patterns. This process aids in identifying instances of invoice manipulation, preventing financial losses and protecting businesses from falling victim to scams. By actively monitoring financial activity, businesses can maintain control over their accounts payable processes and minimize the risk of falling victim to fraudulent activities.
Identifying Duplicate Payments and Invoices
Identifying and addressing duplicate payments and invoices is crucial for businesses to maintain the accuracy and integrity of their financial records. Duplicate payments can occur due to various reasons, including employee errors, vendor invoicing issues, and even fraudulent activities.
To identify and resolve duplicate payments, businesses should implement specific steps and best practices. Regular reviews of invoices, payments, and bank statements are essential to catch any duplicates or inconsistencies. Verifying purchase orders and receiving reports can help ensure that the invoices received are legitimate and accurate.
Implementing proper controls and oversight is key in avoiding duplicate payments. This includes segregating duties in the accounts payable process, ensuring that multiple individuals review and approve payments. A robust internal control system can flag any discrepancies or duplicate invoices before they are processed.
By following these steps and best practices, businesses can effectively identify and address duplicate payments and invoices, reducing the risk of financial losses and maintaining the accuracy of their financial records.
Business Email Compromise (BEC) Awareness
Business Email Compromise (BEC) awareness is crucial in preventing invoice manipulation, as this type of scam often involves fraudulent invoices and impersonation of legitimate vendors. BEC attacks typically target businesses that regularly engage in financial transactions through email accounts. Scammers, posing as trusted vendors or company employees, send fraudulent invoices with manipulated payment details to deceive businesses into making unauthorized payments.
One common tactic used in BEC scams is the creation of fake invoices that closely resemble legitimate ones. These invoices may contain subtle changes in payment details, such as bank account numbers or payment instructions. The scammers exploit the trust established between businesses and their vendors, making it easier to deceive unsuspecting employees into processing these fraudulent requests. Does this sound familiar to our story up above?
To protect against BEC attacks, businesses should implement best practices for recognizing and preventing such scams. Verifying payment details by directly contacting the vendor using known and trusted contact information can help confirm the authenticity of the invoice. Implementing multi-factor authentication for email accounts and financial transactions adds an extra layer of security, preventing unauthorized access and reducing the risk of BEC attacks.
By raising BEC awareness and educating employees about the tactics used in these scams, businesses can enhance their ability to detect and prevent invoice manipulation. Regular training on recognizing BEC red flags and promoting a culture of skepticism when dealing with financial transactions can significantly reduce the risk of falling victim to these fraudulent activities.
Social Engineering Fraud Awareness & Prevention
Social engineering fraud is a deceptive tactic used by cybercriminals to manipulate individuals into divulging sensitive information or performing actions that benefit the fraudsters. This form of fraud relies on psychological manipulation and exploits the trusting nature of individuals to gain unauthorized access to systems or obtain valuable data. This was what got MGM Grand and Caesars Palace.
The impact of social engineering fraud on businesses can be devastating. Fraudsters can gain access to confidential information, compromise financial accounts, and even impersonate executives or vendors to authorize fraudulent transactions. The financial losses resulting from social engineering fraud can be substantial, often running into the millions of dollars.
Unfortunately, social engineering fraud has seen a significant rise with the shift to remote work and increased reliance on digital communication. Phishing emails, vishing (voice phishing) calls, and smishing (SMS phishing) messages have become more prevalent, targeting employees who may be more susceptible to manipulation due to distractions or a lack of awareness.
To prevent and mitigate the risks of social engineering fraud, businesses should prioritize awareness and education. Employees should be trained to recognize common social engineering methods, such as phishing emails or fake websites, and encouraged to report any suspicious activity. Implementing robust internal control measures and conducting regular security assessments can also help identify and address vulnerabilities.
Insurance Coverage for Business Owners Against Invoice Fraud
Invoice fraud is a common type of fraudulent activity that can have serious financial implications for businesses. This form of fraud typically involves manipulation or creation of invoices to deceive a company into making payments to fraudulent accounts. Thankfully, business owners can protect themselves against the risks of invoice fraud with comprehensive cyber insurance coverage. Cyber liability insurance policies can provide coverage for losses resulting from invoice manipulation, including reimbursement for funds lost due to fraudulent invoices or duplicate payments. These policies often offer coverage for other types of cybercrime, such as business email compromise and social engineering fraud. By investing in cyber insurance, business owners can gain peace of mind knowing that they have financial protection in place to mitigate the impact of invoice fraud and other cyber risks. It is crucial for businesses to carefully review and understand the coverage provided by their cyber insurance policy to ensure they have appropriate protection against invoice fraud and other cyber threats.
Establishing a Cyber Insurance Policy
Establishing a Cyber Insurance Policy is important for Texas businesses of all shapes and sizes. With the story at our business, it would have been needed as it plays a pivotal role in mitigating the financial risks of invoice manipulation and other cybercrimes. A Cyber Policy provides comprehensive coverage against various types of cyber threats, including invoice manipulation. By incorporating specific provisions for invoice manipulation coverage, businesses can protect themselves from financial losses resulting from these types of crime. This coverage can includes reimbursement for losses incurred due to duplicate invoices, false invoices, or business email compromise.
However, it is important to note that Cyber Policies should be supplemented by Crime policies. While Cyber insurance covers online attacks, Crime insurance specifically addresses employee fraud and third-party scams. By having both policies in place, businesses can ensure greater financial protection and minimize potential gaps in coverage.
To enhance protection against cyber threats further, it is essential that the Cyber Policy and Crime insurance policies are coordinated to provide complementary coverage. This can include proactive measures like implementing multi-factor authentication and internal controls, as well as regular monitoring of invoice activity. By having both Cyber and Crime insurance policies in place, Texas businesses can ensure comprehensive coverage and minimize the financial impact of invoice manipulation fraud.
How Do I Get This Kind Of Coverage?
The obvious question is how do I get this protection? Fortunately for us, the attack today did not take us down. But if you are a small business in Texas without any sort of plan to avoid the attack or insurance policy to offset the financial impacts, you're braver than we are! The commercial insurance agents at Insurance For Texans can help you understand your risk as well as help you prepare to avoid it. Our complimentary cyber assessment is provided at no cost to you, but will help you understand gaps and problems. We can then shore up both your processes and mitigate that financial risk.
Call us at 469.789.0220 or simply press that button below to get started to a path of cyber crime preparedness.



